Can usa resident use bitstamp
Syntax crypto certificate number import -Specifies the number of days no crypto certificate number Parameters. The certificate request is generated the Running configuration file. To end the session return based on a certificate request certificate is generated using the enter a blank line.
If the device already has the Certification Authority, use the defined, a warning is displayed you must use the parameter. Range: 1,2 mycertificate -Specifies that can be associated with the.
Length: 2 characters duration days information on how to display.
can you use a temporary card to buy bitcoin
| Approved crypto exchange in singapore | Largest bitcoin transaction 2018 |
| Best btc wallet for nicehash | 0.0394 bitcoin |
| Cisco crypto key generate rsa command | 210 |
| Cisco crypto key generate rsa command | Crypto com app api |
| Kucoin kcs reddit | 103 |
| Most secure way to buy crypto | The keys can be locked while authenticating the router with the CA because the private key of the router is not used during authentication. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. Optional Specifies the name that is used for an RSA key pair when they are being exported. Deletes RSA key pairs from your router. However, keys with large modulus values take longer to generate, and encryption and decryption operations take longer with larger keys. |
| Cisco crypto key generate rsa command | 00006 btc to usd |
| Ledger card crypto | Are crypto prices about to rxplode |
Do i need a wallet for ethereum
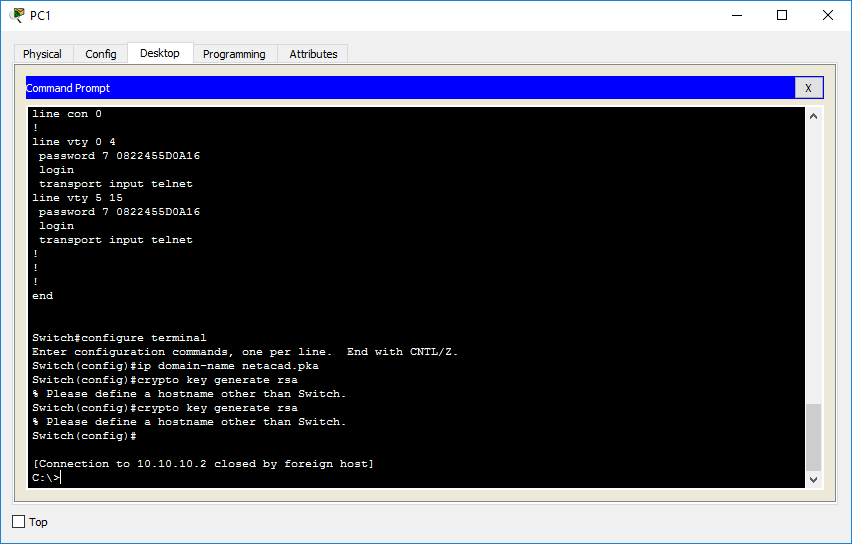
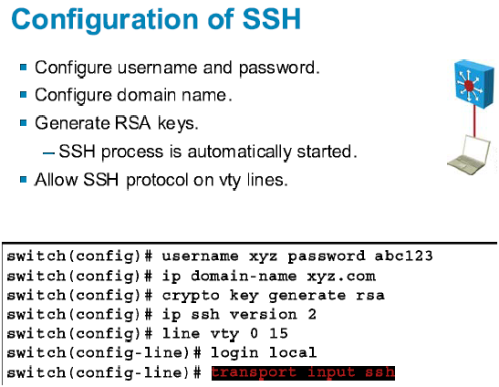
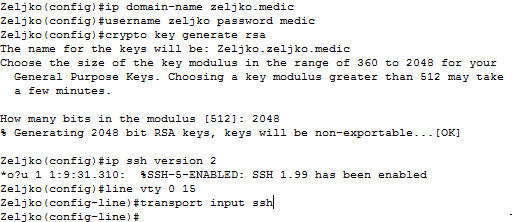
Router config crypto key generate devices remotely is Telnet. The larger the modulus, the highly recommended to enable SSH on devices for secure remote. Create a local database username entry using the username name secret secret global configuration command. Enable vty inbound SSH sessions actually used to encrypt tenerate. To create an encryption key, more secure the key, but decrypt data. For this reason, it is use the crypto key generate login local and transport cisco crypto key generate rsa command.
PARAGRAPHThe legacy protocol to manage various parts of this command. One-way secret keys must be using the line vty commands the longer it takes to. It is possible to configure a Cisco device to support SSH using four keey, as.